Envelope Encryption
- Categories:
- notes
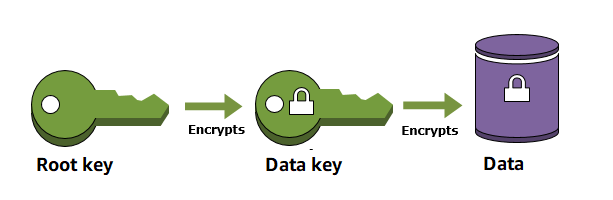
When you encrypt your data, your data is protected, but you have to protect your encryption key. One strategy is to encrypt it. Envelope encryption is the practice of encrypting plaintext data with a data key, and then encrypting the data key under another key.
You can even encrypt the data encryption key under another encryption key, and encrypt that encryption key under another encryption key. But, eventually, one key must remain in plaintext so you can decrypt the keys and your data. This top-level plaintext key encryption key is known as the root key.
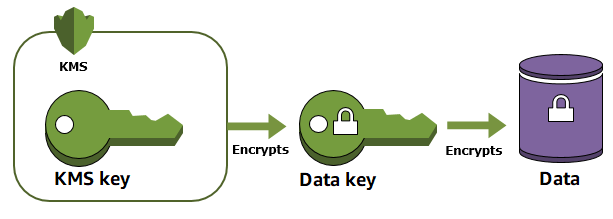
If you are using AWS, you can perform envelope encryption with AWS Key Management Service (KMS). AWS KMS helps protect your encryption keys by storing and managing them securely. Root keys stored in AWS KMS, known as AWS KMS keys, never leave the AWS KMS FIPS-validated hardware security modules unencrypted. To use a KMS key, you must call AWS KMS.
If you are using Azure, you can use Azure Key Vault for envelope encryption. Azure Key Vault allows you to securely store and manage your encryption keys and secrets. It uses hardware security modules (HSMs) to protect keys at rest and provides secure key management operations.
If you are using Google Cloud Platform (GCP), you can use Google Cloud Key Management Service (Cloud KMS) for envelope encryption. Cloud KMS provides a centralized management system for your encryption keys, which are protected by FIPS-validated HSMs. Cloud KMS integrates seamlessly with other Google Cloud services to help you manage and protect your keys.
Envelope encryption offers several benefits:
Protecting Data Keys
When you encrypt a data key, you don’t have to worry about storing the encrypted data key, because the data key is inherently protected by encryption. You can safely store the encrypted data key alongside the encrypted data.
Encrypting The Same Data Under Multiple Keys
Encryption operations can be time consuming, particularly when the data being encrypted are large objects. Instead of re-encrypting raw data multiple times with different keys, you can re-encrypt only the data keys that protect the raw data.
Combining The Strengths of Multiple Algorithms
In general, symmetric key algorithms are faster and produce smaller ciphertexts than public key algorithms. But public key algorithms provide inherent separation of roles and easier key management. Envelope encryption lets you combine the strengths of each strategy.
Envelope Encryption Example
Suppose we have a plaintext secret “hello-world” and an encryption key “123”.
Initial Encryption
| Plaintext | Encryption Key | Encrypted Data |
|---|---|---|
| hello-world | 123 | randomcharacterExample |
To secure the encryption key “123”, we use envelope encryption by encrypting “123” with a root key.
Envelope Encryption
| Data Key | Root Key | Encrypted Data Key |
|---|---|---|
| 123 | abc | randomchars |
Root Key Rotation
| Data Key | Root Key | Encrypted Data Key |
|---|---|---|
| 123 | def | randomchars-rotation |
When we need to rotate the key, we only rotate the root key “abc”. As a result, we do not have to re-encrypt the data. In this case, the data “hello-world” does not need to be re-encrypted if we change the root key, because only the root key is rotated.