DevSecOps
- Categories:
- notes
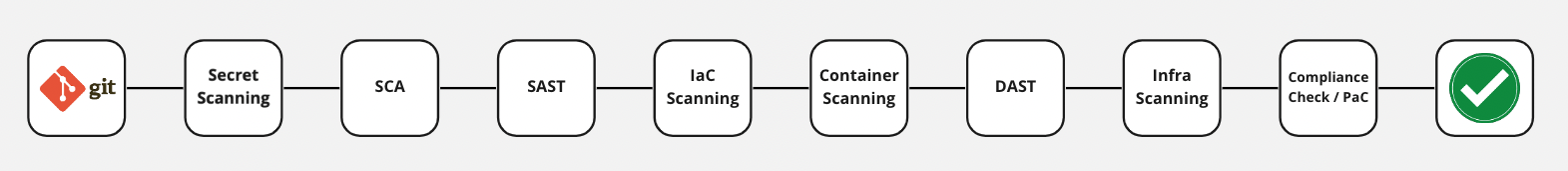
In my recent exploration of DevSecOps, below are key practices that can elevate our application security:
Scan git repositories for finding potential credentials leakage. Implement automated tools to detect hard-coded secrets and review commit histories for potential leaks.
SAST (Static Application Security Test). Analyzes your source code for vulnerabilities without executing the program.
SCA (Software Composition Analysis or dependency check). Evaluates third-party libraries and components used in application.
IAST (Interactive Application Security Testing). Automated test, human tester, or any activity “interacting” with the application functionality.
DAST (Dynamic Application Security Test). Checks vulnerabilities (such has XSS) in your running applications.
IaC Scanning (Scanning Terraform, HelmChart code to find misconfiguration).
Infrastructure scanning. Beyond IaC, scanning the actual infrastructure (including networks, servers, and containers) for vulnerabilities is crucial. This practice ensures that your deployed environment is secure and free from common threats and misconfigurations.
Compliance check. Regular compliance checks ensure that our application and infrastructure adhere to industry standards and regulatory requirements
- Tags:
- #security
- #devsecops